Abstract cyber security with phone and icons concept And internet protection systems Data importing or exiting various devices. 8551663 Vector Art at Vecteezy

Cyber Security System Concept. Mobile Phone with Padlock on Screen. Vector Stock Vector - Illustration of flat, confidential: 102792472

Cyber Security and Mobile Device Management - Cyberhunter Cyber Security | Network Security, Cloud Security & Website Security | Penetration Testing | Vulnerability Assessments | Threat Hunting

Mobile device security. cyber security concept. protecting personal information and data with smartphone. illustration of big screen phone with padlock used by business people Stock Vector | Adobe Stock

4 in 10 smartphones are vulnerable to cyber attacks. Here's how to protect your device - The Economic Times



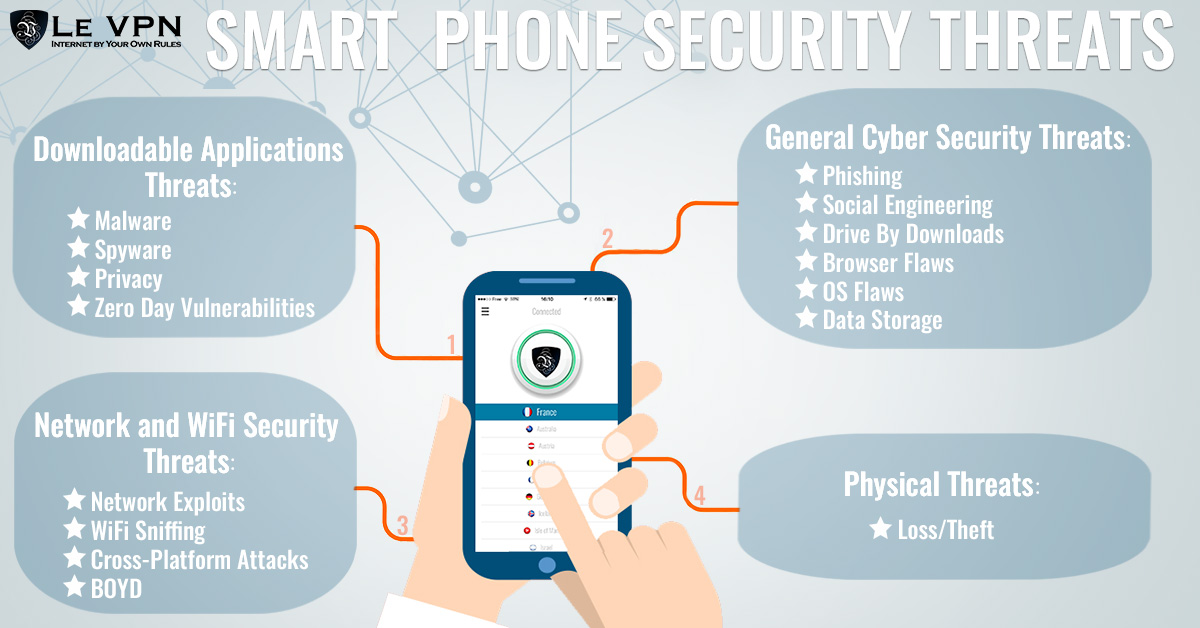









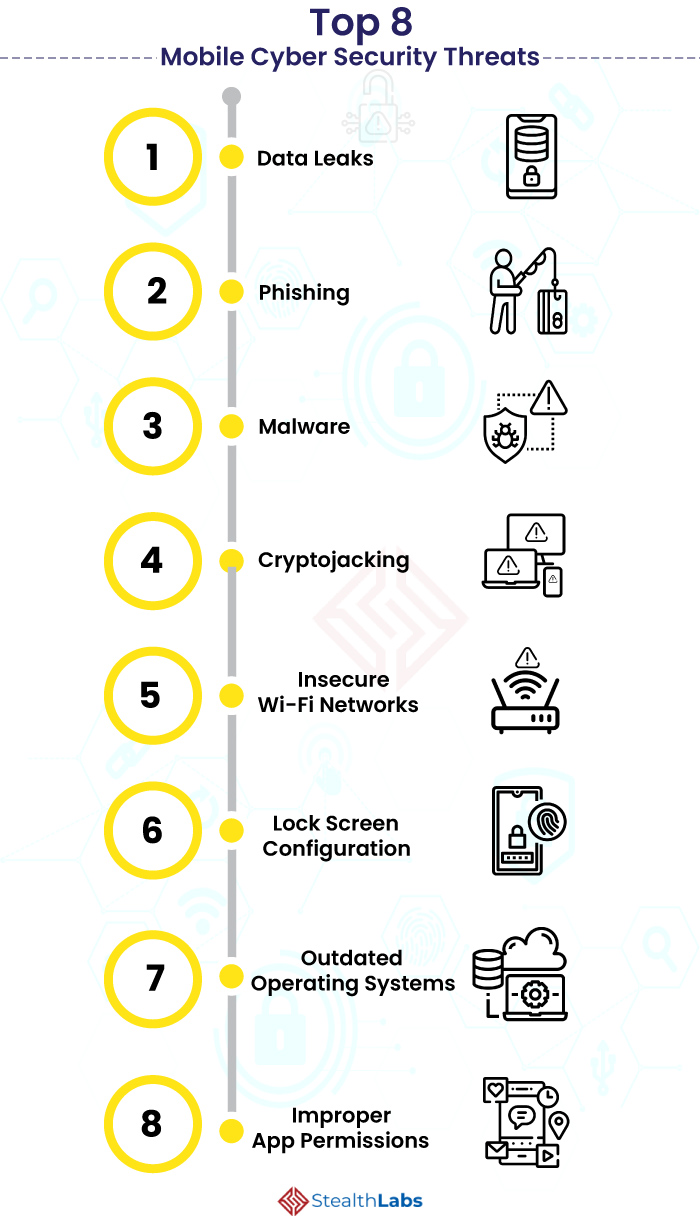
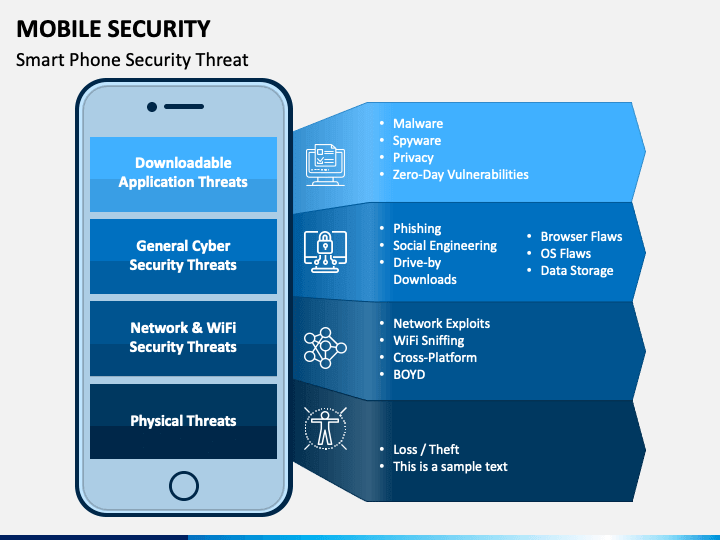





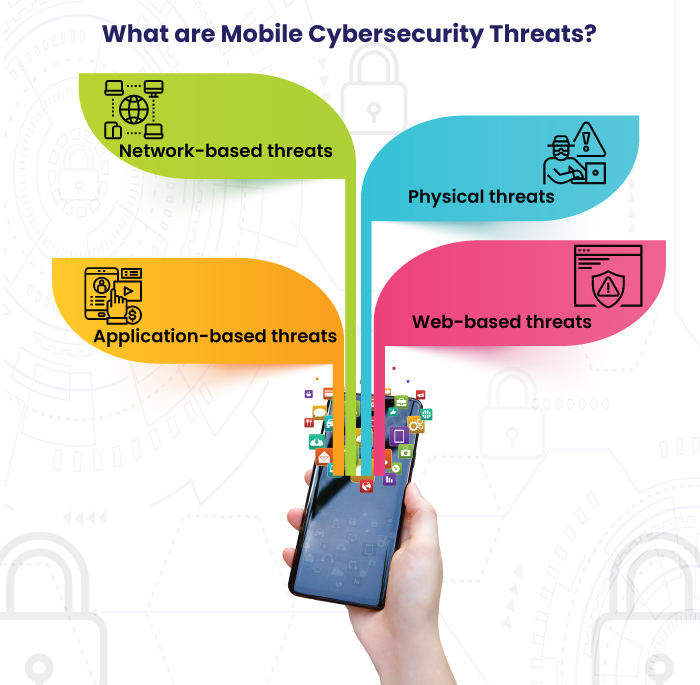
.jpg)