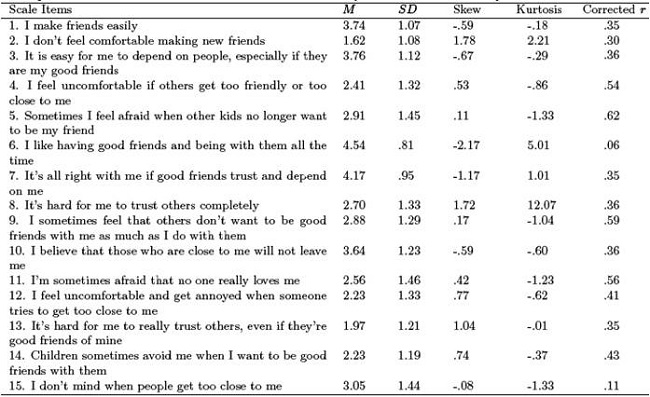
![PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/cfec0b60ee965e255db5a86121bc2031c37642e5/11-Table4-1.png)
PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar
![PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/cfec0b60ee965e255db5a86121bc2031c37642e5/9-Figure1-1.png)
PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar

Scales of Knowledge and Confidence in Safety, Security & Risk Assessments Must Include Calculations of What is Not Known, Unsure, Concealed or False
Attachment Style Classification Questionnaire for latency age: Psychometrics properties of Argentine Sample